Cyber Security
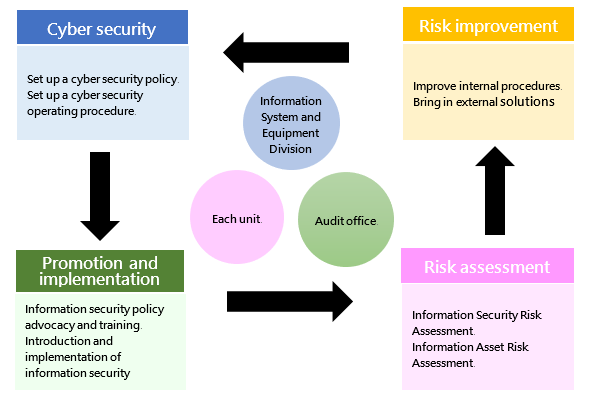
1. Cyber security management strategy and structureThe unit in charge of information security of the Company is the Information System and Equipment Division, which is staffed with one director and several professional information personnel, is responsible for formulating internal information security policies, planning and implementing information security operations, and the promotion and implementation of information security policies, reports the Company's information security governance overview to the Audit Committee.
The Company's information security supervision and inspection unit is the Audit Office, which is staffed with one audit director and several dedicated auditors, is responsible for supervising and inspecting the implementation of internal information security matters. If relevant deficiencies are found in the inspection, the inspected unit will be required to submit relevant improvement plans and specific actions, which will be tracked for the improvement results so as to reduce internal information security risks.
Organizational operation mode - The PDCA cycle management is adopted to ensure the achievement of reliability goals and continuous improvement.
 2. Cyber security policy
2. Cyber security policyIn order to implement the effective operation and implementation of UVB's various information management systems, we maintain the confidentiality, integrity, and availability of important information systems so as to ensure the safe operations of information systems, equipment, and networks.
UVB has established an information security management mechanism, including the following three major items:
(1) System norms: Formulate the Company's information security management systems and guidelines, and standardize the information-related operation behavior of colleagues.
(2) Application of new technology: Import and build information security management related software and hardware, and implement information security management measures.
(3) Personnel training: Regularly conduct information security education and training to enhance the information security concept of all colleagues and implement various information security measures.
Described as follows:
• System norms: The Company has formulated a number of information security management guidelines and systems to regulate the information security behavior of the Company's personnel. It regularly inspects whether the relevant systems conform to the changes in the operating environment every year, and makes adjustments in a timely manner according to needs.
• Application of new technology: In order to prevent various internal and external information security threats, in addition to adopting a multi-layer network architecture design, the Company also builds various information security protection systems and mechanisms, such as high reliability architecture (HA) of high availability, host environment backup, data backup (transaction records, differential backup, and full backup), off-site backup mechanism to improve the security of the overall information environment. In addition, in order to ensure that the operation behavior of internal personnel conforms to the Company's system norms, asset management system tools are also introduced to implement equipment and personnel information security management measures.
• Personnel training: The Company regularly organizes information security education and training courses and establishes an online learning (E-Learning) system to enhance internal personnel information security knowledge and professional skills.
| Information Security Management Measures | ||
|---|---|---|
| Type | Description | Relevant operations |
| Authority management | Management measures for personnel account, authority management, and system operation behavior | Personnel account permission application management and review Regular personnel account permissions inventory |
| Access control | Control measures for personnel access to internal and external systems and data transmission channels | Internal / external access control measures Operation behavior tracking record |
| External threat | Internal potential weaknesses, poisoning channels, and protective measures | Host / computer vulnerability inspection and update measures Virus protection and malware detection Malicious attacks prevention equipment |
| System availability | System availability status and handling measures when service is interrupted | Routine inspection of computer room System / network availability monitoring and reporting mechanism Response measures to service interruption Information backup, local / remote backup mechanism, regular data restoration test Host restore test Regular disaster recovery drills |
• In April 2023: Company-wide "Computer Network Information Security Operations Awareness Campaign."
• In December 2023: Appointed an Information Security Manager and dedicated personnel to oversee the development of information security initiatives, with a budget exceeding NT$6 million for updates to information security software and hardware.
• In May 2024: Conducted "Information Security Awareness" on-the-job training courses for current employees, with a total of 292 participants as of December 31, 2024.
• In the year 2024: Held "Information Security Awareness" onboarding training courses for new employees, with a total of 75 participants as of December 31, 2024.
• In the year 2024: Conducted "Personal Data Protection Act" onboarding training courses for new employees, with a total of 75 participants as of December 31, 2024.
The company has introduced the ISO 27001 international standard for information security management and obtained third-party verification in August 2023. The validity period of the certificate is from August 29, 2023 to October 31, 2025. Through the introduction of the ISO27001 information security management system, we strengthen the ability to respond to information security incidents, maintain the confidentiality, integrity, availability and legality of the company's information, as well as protect customers' personal data.
【Certificate of ISO 27001】【UVB information security elements】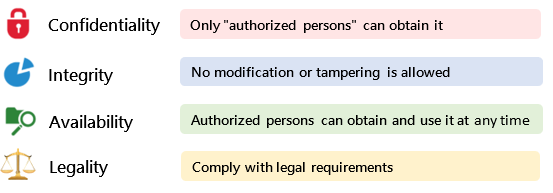 6. Professional Development and Certification of Cyber Security Manager and PersonnelCyber Security Manager:
6. Professional Development and Certification of Cyber Security Manager and PersonnelCyber Security Manager:May 2024: Attended the 10th Taiwan Cyber Security Conference(CYBERSEC 2024).
Cyber Security Personnel:
March 2024: Completed a 12-hour iPAS Information Security Engineer course and obtained the Ministry of Economic Affairs Industry Talent Competency Certification for "Information Security Engineer—Basic Competency."
September 2024: Completed a 40-hour ISO/IEC 27001:2022 Information Security Management System (ISMS) Lead Auditor Training Course and obtained certification. This certification is valid for five years and is applicable to the CQI/IRCA Auditor certification scheme.